This study addresses the growing need for effective cybersecurity solutions by designing an open-source Security Operations Center (SOC) tailored for small and medium-sized enterprises. Recognizing the increasing frequency and sophistication of cyberattacks—ranging from ransomware to SQL injections—the proposed architecture integrates multiple components to ensure comprehensive … [Read more...] about Design and Implementation of an Open-Source Security Operations Center for Effective Cyber Threat Detection and Response
cybersecurity
AI Security: Risks, Frameworks, and Best Practices
AI security encompasses a range of measures designed to protect AI systems from unauthorized access, manipulation, and malicious attacks. These safeguards ensure the integrity, privacy, and proper functioning of AI applications, which are increasingly integral to modern operations. The risks extend beyond technical vulnerabilities to ethical concerns, such as bias and … [Read more...] about AI Security: Risks, Frameworks, and Best Practices
How to create a third-party risk management policy
Developing an effective third-party risk management policy is essential for organizations seeking to mitigate risks from suppliers, vendors, and external partners. These risks include data breaches, operational failures, regulatory violations, and reputational harm. Leveraging NIST’s Cybersecurity Framework (CSF) offers a flexible and globally recognized approach to structuring … [Read more...] about How to create a third-party risk management policy
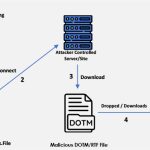
The Mechanics of Remote Template Injection Attack
Remote Template Injection is a sophisticated cyberattack method that exploits Microsoft Word’s ability to load templates from remote servers. Attackers embed a malicious template link in a Word document, enabling the execution of harmful macros without directly embedding them in the file. This allows the decoy document to bypass traditional security measures, including email … [Read more...] about The Mechanics of Remote Template Injection Attack
CMMC 2.0: Your Comprehensive Guide to Certification and Compliance
CMMC 2.0 ensures that any organization working with the Department of Defense (DoD) and handling Federal Contract Information (FCI) or Controlled Unclassified Information (CUI) meets stringent cybersecurity requirements. The updated framework, based on NIST 800-171 standards, reduces complexity by consolidating five certification levels into three. This revision benefits small … [Read more...] about CMMC 2.0: Your Comprehensive Guide to Certification and Compliance
The Rise of Agentic AI: How Hyper-Automation is Reshaping Cybersecurity
Agentic AI is reshaping cybersecurity and the workforce, offering unprecedented efficiency by enabling systems to perform tasks autonomously. Unlike traditional automation, which relies on predefined workflows, agentic AI dynamically adapts and collaborates across domains, handling complex tasks such as incident remediation and threat hunting without constant human … [Read more...] about The Rise of Agentic AI: How Hyper-Automation is Reshaping Cybersecurity
The Hard Truth About Breaking Into Cybersecurity
Breaking into cybersecurity has become more competitive than ever, as the market is saturated with candidates holding standard certifications like Security+ or CySA+. While certifications are still important, they are no longer enough. Employers now seek candidates with degrees, practical experience, and specialized skills to stand out in this crowded field. Degrees from … [Read more...] about The Hard Truth About Breaking Into Cybersecurity
The Ultimate SaaS Security Admin Guide for 2025
SaaS security involves securing access to and using cloud-based applications to protect against unauthorized access, data breaches, and other cyber threats. It relies on the shared responsibility model, where cloud service providers ensure infrastructure security while customers manage data and application security. Critical elements include encryption, backups, multi-factor … [Read more...] about The Ultimate SaaS Security Admin Guide for 2025
A Deep Dive into ISO 27001 Password Requirements
ISO 27001 underscores the critical role of password management in safeguarding sensitive data and achieving a strong security posture. It encourages organizations to develop password policies emphasizing complexity, minimum character lengths, and multi-factor authentication while promoting regular reviews and updates to stay ahead of evolving threats. Shared accounts are … [Read more...] about A Deep Dive into ISO 27001 Password Requirements
Key steps to scaling automated compliance while maintaining security
Organizations face technical, operational, and resource challenges when implementing scalable , automated compliance frameworks. These include integrating data from diverse sources, managing vendor onboarding, and tailoring systems to specific organizational needs. Effective strategies involve leveraging automation to streamline processes, implementing tiered risk assessments, … [Read more...] about Key steps to scaling automated compliance while maintaining security
CISA Releases National Cyber Incident Response Plan update
The NCIRP serves as a strategic national framework for addressing cyber incidents, focusing on coordination between public and private stakeholders under the guidance of Presidential Policy Directive 41 (PPD-41). It aims to enhance national preparedness by leveraging contributions from various entities and aligning their efforts during significant cyber incidents. This plan … [Read more...] about CISA Releases National Cyber Incident Response Plan update
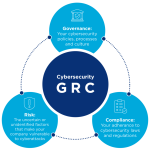
Does an actually decent GRC platform exist?
Some widespread frustration exists with Governance, Risk, and Compliance (GRC) platforms, which many find inflexible or overly complex. Critics pointed to issues such as a lack of adaptability, poor evidence integration for audits, and a focus on compliance that overlooks governance and risk management. While some platforms like ZenGRC, Hyperproof, and OneTrust were mentioned … [Read more...] about Does an actually decent GRC platform exist?
Breaking Into the U.S. Market: Cybersecurity Compliance to Fuel International Growth
Expanding into the U.S. market presents significant growth opportunities for Europe-based cloud service providers (CSPs), but achieving success requires aligning with American cybersecurity compliance expectations. Unlike the EU’s GDPR, the U.S. lacks a comprehensive national privacy law, making adherence to voluntary frameworks such as SOC 2 and ISO 27001 essential for … [Read more...] about Breaking Into the U.S. Market: Cybersecurity Compliance to Fuel International Growth
CISA, JCDC, Government and Industry Partners Publish AI Cybersecurity Collaboration Playbook
The AI Cybersecurity Collaboration Playbook, released by the Cybersecurity and Infrastructure Security Agency (CISA) through the Joint Cyber Defense Collaborative (JCDC), offers critical guidance for managing cybersecurity risks in AI systems. Designed for AI providers, developers, and adopters, the playbook promotes voluntary sharing of actionable information related to AI … [Read more...] about CISA, JCDC, Government and Industry Partners Publish AI Cybersecurity Collaboration Playbook
A Catalog of ISO 27002 Controls
ISO/IEC 27002:2022 is a widely recognized international standard that outlines best practices for implementing information security controls. It supports organizations in mitigating risks to information assets, whether physical, digital, or intellectual. The standard’s 93 controls are categorized into organizational, people, physical, and technological domains, with additional … [Read more...] about A Catalog of ISO 27002 Controls
Common Mistakes in ISO 27001 Implementation and How to Avoid Them
ISO 27001 implementation is critical for establishing a robust Information Security Management System (ISMS), but organizations often encounter common pitfalls that hinder success. One major issue is insufficient management commitment, as leadership involvement is vital for driving cultural and operational changes. Another frequent mistake is poorly defining the ISMS scope, … [Read more...] about Common Mistakes in ISO 27001 Implementation and How to Avoid Them
Securing Non-Human Identities (NHIs) and ISO 27001 Compliance
Securing non-human identities is a critical yet often overlooked aspect of ISO 27001 compliance. These identities, encompassing machine credentials such as API keys, service accounts, and IoT devices, facilitate automated processes and machine-to-machine interactions but also present security vulnerabilities due to their elevated access rights. Compromise of these identities … [Read more...] about Securing Non-Human Identities (NHIs) and ISO 27001 Compliance
How to Write an ISO 27001 Statement of Applicability
The ISO 27001 Statement of Applicability (SoA) is a key document that outlines which of the 93 Annex A controls apply to your organization and why. It defines the scope of your information security management system (ISMS), helps set priorities for implementation, and provides a framework for internal and external audits. The SoA ensures your approach to information security … [Read more...] about How to Write an ISO 27001 Statement of Applicability
Cybersecurity & Data Protection Assessment Standards (CDPAS) to standardize third-party assessments for cybersecurity
The Cybersecurity & Data Protection Assessment Standards (CDPAS), created by the SCF Council, aim to provide a unified and consistent framework for conducting third-party assessments, attestation, and certification services in cybersecurity and data protection. These standards address the fragmented approaches currently used, ensuring assessments meet predefined quality and … [Read more...] about Cybersecurity & Data Protection Assessment Standards (CDPAS) to standardize third-party assessments for cybersecurity
Generative AI and IT Governance: Friends or Foes? Navigating the Future of Generative AI and Information Governance
Generative AI’s transformative potential will depend on how organizations integrate information governance into their operations. Governance frameworks will address risks like bias, data misuse, and regulatory challenges while ensuring compliance, ethical practices, and trust. Ethical AI will become a necessity, requiring audits for fairness, transparency protocols, and … [Read more...] about Generative AI and IT Governance: Friends or Foes? Navigating the Future of Generative AI and Information Governance