SOC 2 Compliance Audit is crucial in ensuring businesses protect vast client information in today’s interconnected digital world. SOC 2, for System and Organization Controls 2, is an auditing procedure developed by the American Institute of CPAs (AICPA). It provides a framework to assess an organization’s controls for security, availability, processing integrity, … [Read more...] about What is SOC 2 Compliance Audit?
An Audit Handbook for Segregation of Duties
Ineffective segregation of duties (SoD) in enterprise applications can lead to operational losses, financial misstatements, and fraud. The rapid addition of users to enterprise applications increases the risk of SoD violations, especially when default roles are not well-configured to prevent such violations. Business managers often struggle to obtain accurate security … [Read more...] about An Audit Handbook for Segregation of Duties
Organizations unready for AI pose increasing security risks
Implementing generative AI technologies in business presents significant cybersecurity risks often overshadowed by the enthusiasm to stay competitive. While generative AI offers benefits like enhanced productivity and improved performance in various sectors, the rapid adoption without adequate safety measures can expose companies to data breaches and malicious attacks. The hype … [Read more...] about Organizations unready for AI pose increasing security risks
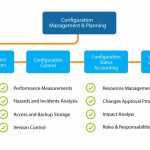
Mastering Configuration Management Across the Modern Enterprise
Security Configuration Management (SCM) is an essential cybersecurity practice for ensuring systems are configured correctly to meet security and compliance standards. SCM helps reduce cyber risks by securing configurations, which involves detecting and remediating misconfigurations across both on-premises and cloud environments. Effective SCM minimizes an organization's attack … [Read more...] about Mastering Configuration Management Across the Modern Enterprise
4 use cases for AI in cyber security
Artificial intelligence (AI) is increasingly integrated into various facets of life, including cybersecurity. AI's ability to simulate human intelligence through pattern recognition, learning, and problem-solving makes it a powerful tool for enhancing product security. In cybersecurity, AI is employed to automate, analyze, and improve processes such as log analysis, threat … [Read more...] about 4 use cases for AI in cyber security
The Fundamentals of Cyber Risk Management
Effective cyber risk management is essential for regulatory compliance and minimizing the impact and frequency of cyber incidents. Many organizations are still not actively managing their cybersecurity postures, which involves continuous monitoring and adjustment rather than a "set and forget" approach. Cyber risk management uses business processes and technical controls to … [Read more...] about The Fundamentals of Cyber Risk Management
NIST cybersecurity framework 2.0 self-scoring tool
Expel's NIST CSF 2.0 self-scoring spreadsheet is designed to help organizations quickly assess their cybersecurity posture according to the latest NIST Cybersecurity Framework (CSF) standards. As a leading Managed Detection and Response (MDR) provider, Expel offers this tool to simplify translating complex NIST CSF standards into actionable insights, including the recent 2.0 … [Read more...] about NIST cybersecurity framework 2.0 self-scoring tool
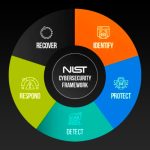
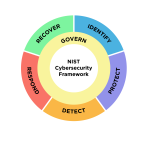
The NIST Cybersecurity Framework (CSF) 2.0
The "NIST Cybersecurity Framework (CSF) 2.0," published by the National Institute of Standards and Technology (NIST), provides a comprehensive guide for organizations to manage and mitigate cybersecurity risks. This framework is designed to be applicable across various industries, government sectors, and organizations of all sizes and maturity levels. It outlines a taxonomy of … [Read more...] about The NIST Cybersecurity Framework (CSF) 2.0
An Under the Hood Look at Operational Technology (OT) Security Software
Operational technology (OT) is the hardware and software that monitors and controls devices, processes, and infrastructure, and is used in industrial settings. It ties together internal and external data between administrative operations and automation, programmable controls, line sensors and other real time data sources and provides increased accuracy, efficiency and reduction … [Read more...] about An Under the Hood Look at Operational Technology (OT) Security Software
Pragmatic ISMS Implementation Guidelines
SecAware's "ISMS Implementation Guidelines" provide a fairly comprehensive, pragmatic approach to applying ISO/IEC 27001 in practice for information risk and security professionals. The document offers detailed guidance on constructing and implementing an Information Security Management System (ISMS) that aligns with the standard’s formal specifications and an organization’s … [Read more...] about Pragmatic ISMS Implementation Guidelines
Data Breach Notification Laws by State
In the United States, personal information is safeguarded by industry-specific federal laws and varying state legislation, each with its own scope and jurisdiction. Consequently, organizations operating nationwide face significant challenges in ensuring compliance. The page below offers a summary of the requirements under each of the 50 state data breach notification laws as … [Read more...] about Data Breach Notification Laws by State
FTC Releases 2023 Privacy and Data Security Update
The Federal Trade Commission (FTC) released its 2023 Privacy and Data Security Update, which outlines the agency's efforts to protect consumer privacy in response to evolving data usage practices, including artificial intelligence (AI) development and health data misuse. The update emphasizes the FTC's proactive measures to address the indiscriminate collection and … [Read more...] about FTC Releases 2023 Privacy and Data Security Update
Cybersecurity on a budget: Evaluating security and performance of open-source SIEM solutions
Researchers are addressing the increasing need for robust cybersecurity measures among Small and Medium Enterprises (SMEs) in the face of evolving cyber threats. Given the budgetary constraints and limited cybersecurity expertise in SMEs, their study focuses on the potential of open-source Security Information and Event Management (SIEM) systems as cost-effective solutions. The … [Read more...] about Cybersecurity on a budget: Evaluating security and performance of open-source SIEM solutions
CNIL Practice Guide to Security of Personal Data in 2024
The "CNIL Practice Guide: Security of Personal Data 2024" provides comprehensive guidelines for organizations to implement security measures ensuring personal data protection as mandated by the GDPR. The guide targets data protection officers (DPOs), chief information security officers (CISOs), IT professionals, and privacy lawyers, offering practical advice and … [Read more...] about CNIL Practice Guide to Security of Personal Data in 2024
An Analysis of the Market for Endpoint Security
Radicati's "Endpoint Security Market Quadrant 2024" report analyzes the current landscape of the endpoint security market, categorizing vendors into four distinct segments: Top Players, Trail Blazers, Specialists, and Mature Players. The report comprehensively evaluates each vendor based on their functionality and strategic vision. It aims to help readers understand the … [Read more...] about An Analysis of the Market for Endpoint Security
A Guide to Traceability in Manufacturing
Traceability in manufacturing refers to the capability to track and document every aspect of the production process, from raw material procurement to the finished product reaching the consumer. This ability is becoming increasingly crucial in various sectors due to the stringent regulations that require detailed tracking to ensure compliance and quality control. Traceability … [Read more...] about A Guide to Traceability in Manufacturing
An Introduction to AIAG & VDA FMEA Methodology
The AIAG & VDA Failure Mode & Effects Analysis (FMEA) represents a significant shift in how Failure Modes and Effects Analysis is approached and applied in various industries. Originally rooted in the automotive sector, FMEA methodologies have broadened to include industries like aviation and medical equipment, highlighting its universal relevance. The AIAG & VDA … [Read more...] about An Introduction to AIAG & VDA FMEA Methodology
Quality of the Future
Quality management (QM) is evolving beyond traditional product-focused methods to embrace comprehensive customer experiences and service integration, reflecting the dynamic nature of customer needs in various industries, including mobility. The study, in collaboration with TU Berlin, highlights the importance of developing QM organizations that are proactive and tailored to … [Read more...] about Quality of the Future
Nine Tips to Better Process Development
Achieving exceptional results in process development requires mastering specific techniques designed to design successful, waste-free processes. The initial step in effective process development is appointing a system architect who can oversee the process's comprehensive and detailed aspects and ensure alignment with broader management systems. Emphasis is placed on developing … [Read more...] about Nine Tips to Better Process Development
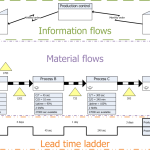
What Is Value Stream Mapping & How Is It Used in Six Sigma
Value Stream Mapping (VSM) is a pivotal tool in Six Sigma, a methodology aimed at improving product quality and efficiency by minimizing errors, variations, and waste. Initially developed in manufacturing environments such as Motorola and later adapted across various industries, including finance and healthcare, VSM is a visual method that analyzes and optimizes the entire flow … [Read more...] about What Is Value Stream Mapping & How Is It Used in Six Sigma