- Remote Template Injection exploits Microsoft Word’s template functionality to deliver malicious payloads, bypassing traditional security measures through seemingly harmless documents.
- Advanced Persistent Threat (APT) groups increasingly use this technique in spear-phishing campaigns, enabling macro execution from remote templates while evading detection systems.
- Mitigation strategies include disabling remote template loading, enhancing email security, user education, and leveraging threat intelligence to monitor evolving tactics.
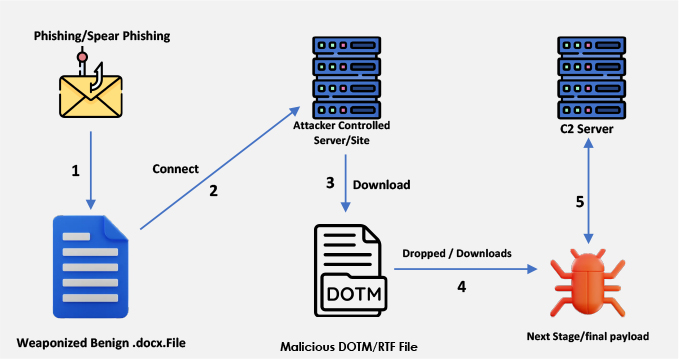
Remote Template Injection is a sophisticated cyberattack method that exploits Microsoft Word’s ability to load templates from remote servers. Attackers embed a malicious template link in a Word document, enabling the execution of harmful macros without directly embedding them in the file. This allows the decoy document to bypass traditional security measures, including email filters and endpoint detection solutions. The technique is particularly effective in spear-phishing campaigns, where attackers manipulate victims into opening these disguised documents, triggering remote code execution. Its effectiveness stems from leveraging trusted, legitimate Office features that blend with standard user activity.
The attack process involves hosting a macro-enabled template file (.dotm) on an attacker-controlled server, embedding its URL within a decoy Word document (.docx), and distributing the document through phishing campaigns. The Word document retrieves and executes the remote template’s malicious code upon opening. Variations in URL formats, such as hexadecimal or decimal IP addresses, further help attackers evade detection. This method’s effectiveness is evident in its use by notable APT groups like FIN7, APT28, and TA505, which have deployed it for delivering ransomware, stealing credentials, and establishing long-term access to target networks.
Mitigating this threat requires proactive measures. Organizations should disable remote template loading in Microsoft Office, strengthen email filtering systems, and train employees to recognize phishing attempts. Monitoring known APT groups through threat intelligence platforms can provide insights into evolving tactics, enabling preemptive defense strategies. Additionally, understanding how attackers manipulate Office document structures—such as altering XML relationship files (.rels)—can help security teams detect and block these attacks more effectively.
Given the growing adoption of Remote Template Injection by cybercriminals, continuous vigilance and layered defenses are crucial. This evolving threat highlights the importance of securing common productivity tools and addressing the human element of cybersecurity through education and awareness. By implementing technical controls and fostering a security-conscious culture, organizations can reduce their exposure to such covert attack methods.


Leave a Reply
You must be logged in to post a comment.