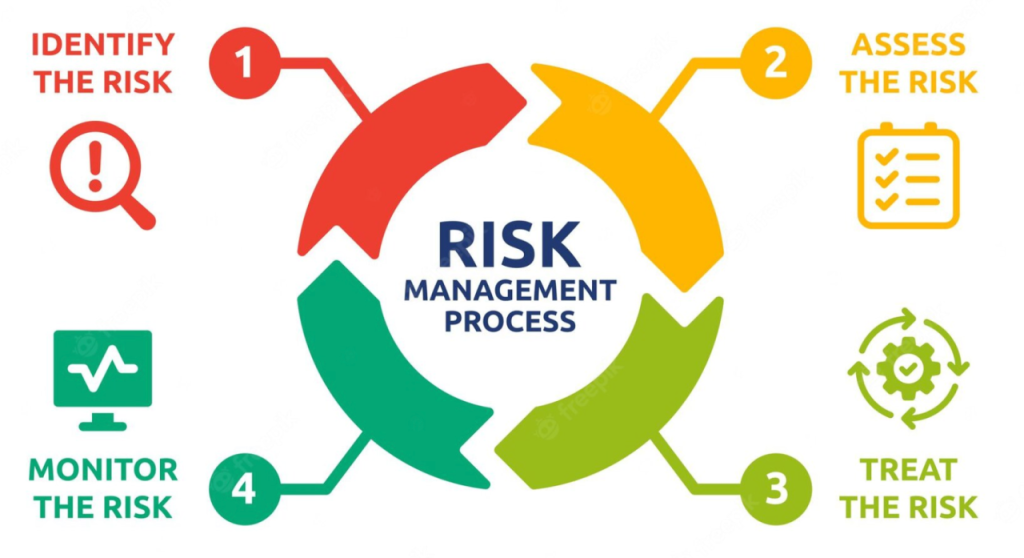
- Cyber risk management uses business processes and technical controls to identify, rank, monitor, and manage the risks associated with an organization’s use of IT and OT systems and the Internet.
- Accountability for cyber risk management should rest with a Chief Information Security Officer (CISO) who understands the organization’s technical and business aspects.
- A comprehensive approach to risk management includes collaboration with all relevant stakeholders and using a Responsible, Accountable, Consulted, and Informed (RACI) assignment matrix to define roles and responsibilities clearly.
Effective cyber risk management is essential for regulatory compliance and minimizing the impact and frequency of cyber incidents. Many organizations are still not actively managing their cybersecurity postures, which involves continuous monitoring and adjustment rather than a “set and forget” approach.
Cyber risk management uses business processes and technical controls to identify, rank, monitor, and manage the risks associated with an organization’s use of IT and OT systems and the Internet. This involves making qualitative and quantitative risk assessments, although the discipline lacks standardized metrics and universally agreed methods for all businesses. Despite this, the NIST Cybersecurity Framework is recognized as a valuable tool for guiding cyber risk management efforts, even though it requires customization to fit the specific needs of different organizations.
Accountability for cyber risk management should rest with a Chief Information Security Officer (CISO) who understands the organization’s technical and business aspects. Effective cyber risk management requires the CISO to have the full support of management and the board, ensuring that cyber risk management is integrated into the organization’s overall risk management strategy. A comprehensive approach to risk management includes collaboration with all relevant stakeholders and using a Responsible, Accountable, Consulted, and Informed (RACI) assignment matrix to define roles and responsibilities clearly.
Maintaining a high-fidelity asset inventory as the foundation for effective cyber risk management is also essential. This inventory should include not just traditional IT assets but also all other assets that could be exploited by cyber threats. Continuous monitoring and managing these assets are crucial, as the dynamic nature of IT environments means that security postures can drift from their intended states. Automation plays a crucial role in managing this complexity, helping identify and promptly mitigate new risks. Organizations should adopt a continuous and iterative approach to cyber risk management, adjusting their strategies to stay ahead of evolving threats.


Leave a Reply
You must be logged in to post a comment.