- Retail supply chains face significant cybersecurity risks, requiring robust frameworks for managing supplier, service, and software vulnerabilities.
- Effective cybersecurity management includes categorizing risks, conducting due diligence, and implementing contractual provisions, access controls, and ongoing monitoring.
- Authoritative frameworks and tools, such as NIST guidelines and continuous monitoring technologies, are essential for enhancing supply chain security and mitigating threats.
- While this paper addresses retail business, these validation processes can apply to many business types within business-to-business (B2B), government, and vendor/supplier chains.
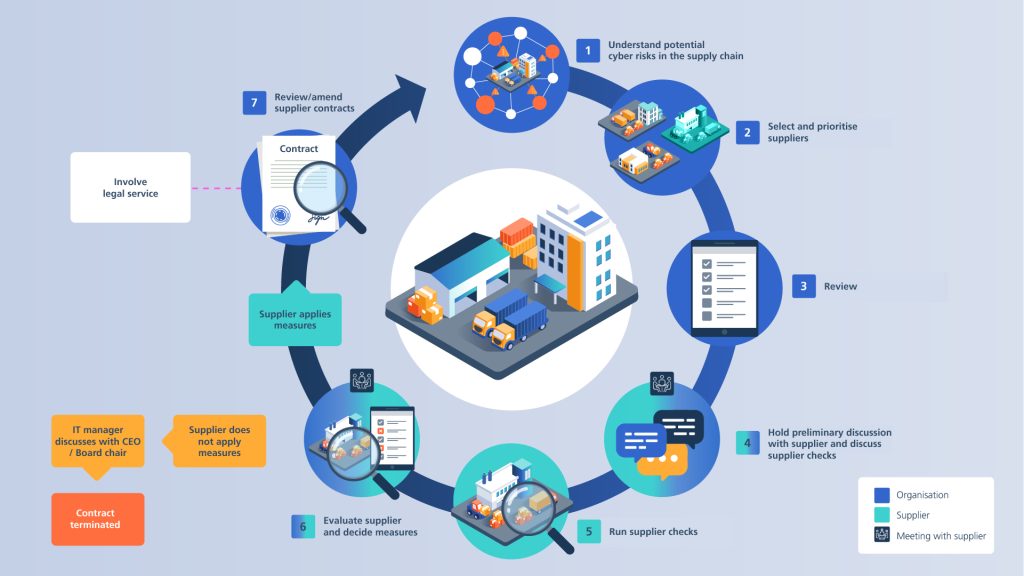
Retail supply chains rely heavily on third-party suppliers, creating potential cybersecurity vulnerabilities that malicious actors can exploit. Risks are categorized into supplier, supply, and service risks, each requiring tailored strategies to mitigate threats. High-risk suppliers, such as those handling critical software or sensitive data, necessitate rigorous evaluation and monitoring. A structured risk management framework prioritizes resources based on a supplier’s criticality and the potential impact of an incident, addressing operational, legal, and reputational risks.
Proactive due diligence is essential in assessing suppliers’ security capabilities and includes evaluating their reputation, compliance history, financial stability, geographic location, and hiring practices. Additional tools like continuous monitoring platforms and Software Bill of Materials (SBOMs) provide real-time insights into vulnerabilities, while frameworks such as NIST and ISO 27001 guide best practices. These measures help illuminate security performance, ensuring transparency and alignment with regulatory standards such as PCI-DSS and HIPAA.
Establishing strong contractual provisions is critical for mitigating supply chain risks. Contracts should define required security controls, data protection policies, and incident response protocols. Service-level agreements (SLAs) should include the right to audit supplier practices and verify compliance with established standards. Enhanced access controls, including multi-factor authentication and least-privilege principles, reduce the risk of misuse or unauthorized access.
Ongoing oversight and monitoring ensure suppliers maintain compliance and adapt to evolving cybersecurity landscapes. Automated tools streamline the management of supplier relationships, providing continuous diagnostics and risk assessments. By leveraging industry standards, emerging technologies, and transparent governance practices, businesses can strengthen their supply chain cybersecurity and minimize the risk of operational disruptions, data breaches, and regulatory penalties.


Leave a Reply
You must be logged in to post a comment.