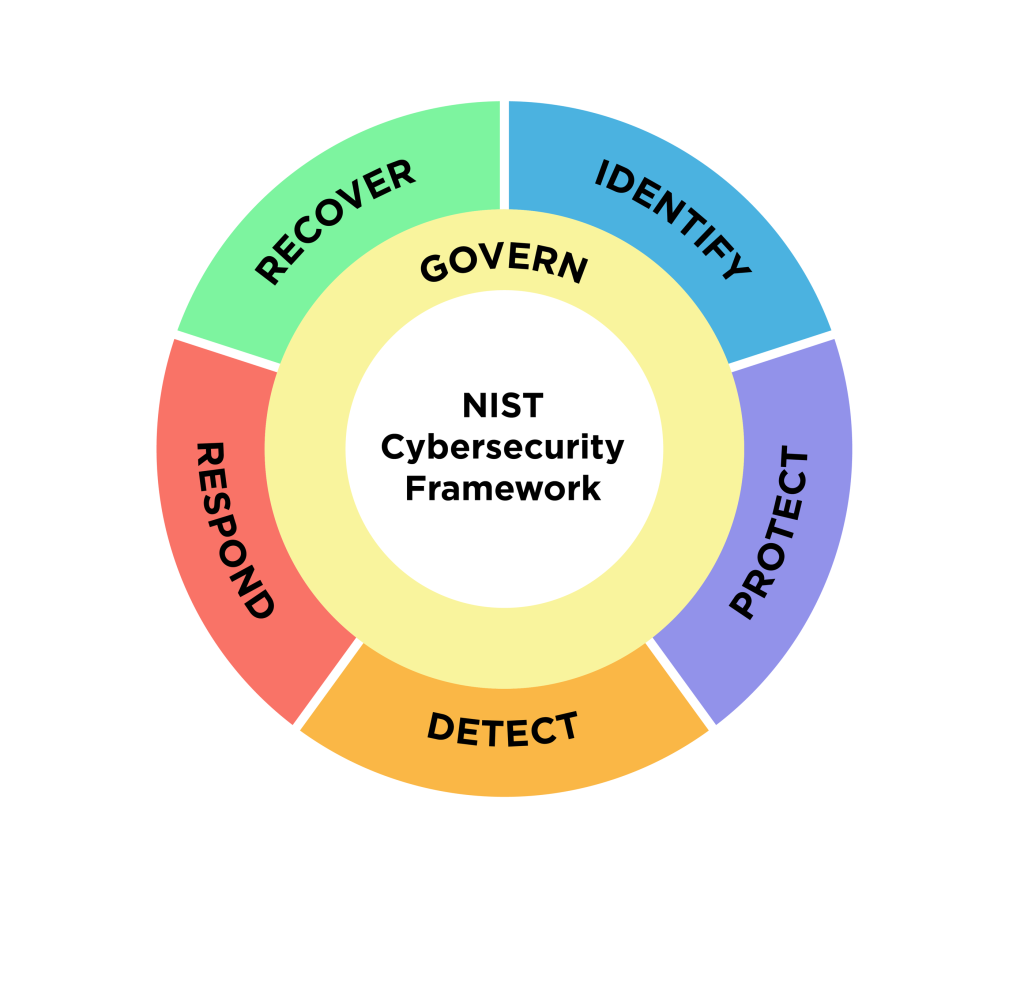
- The “NIST Cybersecurity Framework (CSF) 2.0,” published by the National Institute of Standards and Technology (NIST), provides a comprehensive guide for organizations to manage and mitigate cybersecurity risks.
- The CSF 2.0 comprises six core functions: GOVERN, IDENTIFY, PROTECT, DETECT, RESPOND, and RECOVER. These functions are organized hierarchically into Categories and Subcategories, which detail specific outcomes.
- Governance is emphasized as a critical component of the framework, integrating cybersecurity risk management into broader enterprise risk management strategies.
The “NIST Cybersecurity Framework (CSF) 2.0,” published by the National Institute of Standards and Technology (NIST), provides a comprehensive guide for organizations to manage and mitigate cybersecurity risks. This framework is designed to be applicable across various industries, government sectors, and organizations of all sizes and maturity levels. It outlines a taxonomy of high-level cybersecurity outcomes without prescribing specific methods for achieving them, offering flexibility to tailor its application to unique organizational contexts. Instead, it links to online resources that provide additional guidance on practices and controls to help achieve these outcomes.
The CSF 2.0 comprises six core functions: GOVERN, IDENTIFY, PROTECT, DETECT, RESPOND, and RECOVER. These functions are organized hierarchically into Categories and Subcategories, which detail specific outcomes. The framework also introduces CSF Organizational Profiles, which help organizations describe their current and target cybersecurity postures, and CSF Tiers, which characterize the rigor of an organization’s cybersecurity risk management practices. The core structure aims to help organizations understand, assess, prioritize, and communicate their cybersecurity risks and efforts effectively.
Governance is emphasized as a critical component of the framework, integrating cybersecurity risk management into broader enterprise risk management strategies. The GOVERN function supports establishing, communicating, and monitoring cybersecurity policies and strategies, aligning them with the organization’s mission and stakeholder expectations. IDENTIFY focuses on understanding assets and associated risks, while PROTECT involves implementing safeguards to manage those risks. DETECT enables the timely discovery of cybersecurity incidents, essential for effective incident response (RESPOND) and recovery (RECOVER) efforts.
NIST supplements the CSF with various online resources, including Informative References, Implementation Examples, and Quick Start Guides (QSGs), which provide actionable guidance for achieving the framework’s outcomes. These resources are continuously updated to remain relevant and help organizations tailor the CSF to their specific needs. The CSF encourages continuous improvement and adaptation to evolving cybersecurity threats, making it a valuable tool for organizations to enhance their cybersecurity posture and resilience.


Leave a Reply
You must be logged in to post a comment.