The demand for Governance, Risk, and Compliance (GRC) tools has surged as businesses face mounting regulatory pressures, cybersecurity threats, and stakeholder expectations for ethical conduct. GRC platforms help companies centralize and automate their risk assessments, compliance reporting, and internal controls, transforming what were once disjointed manual processes into … [Read more...] about Top 5 Governance, Risk, and Compliance (GRC) Tools and Solutions for 2025
Cybersecurity-Software
10 Best Vulnerability Assessment and Penetration Testing (VAPT) Tools in 2025
Vulnerability Assessment and Penetration Testing (VAPT) tools are essential for organizations aiming to strengthen their cybersecurity defenses. Vulnerability assessments identify potential weaknesses in systems, while penetration testing simulates attacks to determine if these vulnerabilities are exploitable. Together, they provide a comprehensive security evaluation that … [Read more...] about 10 Best Vulnerability Assessment and Penetration Testing (VAPT) Tools in 2025
Does an actually decent GRC platform exist?
Some widespread frustration exists with Governance, Risk, and Compliance (GRC) platforms, which many find inflexible or overly complex. Critics pointed to issues such as a lack of adaptability, poor evidence integration for audits, and a focus on compliance that overlooks governance and risk management. While some platforms like ZenGRC, Hyperproof, and OneTrust were mentioned … [Read more...] about Does an actually decent GRC platform exist?
Software Acquisition Guide for Government Enterprise Consumers: Software Assurance in Cyber-Supply Chain Risk Management
This Software Acquisition Guide by the ICT SCRM Task Force tackles the need for greater transparency and accountability in technology acquisitions, especially where cybersecurity is concerned. Traditional acquisition processes often leave consumers vulnerable, as they rely on suppliers’ limited disclosures about software development and third-party practices. With a focus on … [Read more...] about Software Acquisition Guide for Government Enterprise Consumers: Software Assurance in Cyber-Supply Chain Risk Management
The State of Software Supply Chain (SSCS) 2024
According to Software Supply Chain (SSC) vendor ReversingLabs, the past year has marked a significant shift in the software supply chain security landscape. High-profile incidents like the 3CX hack and the MOVEit attack underscore the growing vulnerability of software supply chains to malicious actors. These attacks revealed software producers' and consumers' difficulty in … [Read more...] about The State of Software Supply Chain (SSCS) 2024
The Guide to Integration Security for B2B SaaS
Integrations play a critical role in the current technological landscape by enhancing efficiency, data accessibility, scalability, customer experience, cost reduction, innovation, and compliance. However, these integrations also bring various security risks. Common threats include insecure APIs, misconfigurations, insufficient authentication and authorization, data leaks, … [Read more...] about The Guide to Integration Security for B2B SaaS
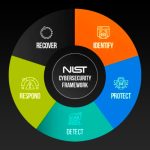
NIST cybersecurity framework 2.0 self-scoring tool
Expel's NIST CSF 2.0 self-scoring spreadsheet is designed to help organizations quickly assess their cybersecurity posture according to the latest NIST Cybersecurity Framework (CSF) standards. As a leading Managed Detection and Response (MDR) provider, Expel offers this tool to simplify translating complex NIST CSF standards into actionable insights, including the recent 2.0 … [Read more...] about NIST cybersecurity framework 2.0 self-scoring tool
An Under the Hood Look at Operational Technology (OT) Security Software
Operational technology (OT) is the hardware and software that monitors and controls devices, processes, and infrastructure, and is used in industrial settings. It ties together internal and external data between administrative operations and automation, programmable controls, line sensors and other real time data sources and provides increased accuracy, efficiency and reduction … [Read more...] about An Under the Hood Look at Operational Technology (OT) Security Software
Getting Started With Passkeys, One Service at a Time
This article by Robert Lemos discusses the growing momentum of passkeys, a technology designed to replace traditional passwords for logging into websites and cloud services. Major technology companies like Apple, Google, Microsoft, and third-party password providers such as 1Password and Bitwarden have embraced passkeys. This widespread adoption is in response to the … [Read more...] about Getting Started With Passkeys, One Service at a Time
The Market Guide for Data Masking
The article delves into the evolution and significance of data masking (DM) in the context of modern data security. With the rapid modernization of data and analytics (D&A) architectures, there's a growing need to mask sensitive data at scale. Data masking is a mature technology that deidentifies data while retaining some analytical capabilities. The rise in privacy … [Read more...] about The Market Guide for Data Masking