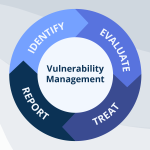
Vulnerability management (VM) is a proactive approach to identifying, evaluating, and mitigating security vulnerabilities within an organization's systems. By continuously scanning and monitoring environments, VM helps minimize attack surfaces and protect critical assets. A risk-based approach, RBVM, enhances traditional methods by prioritizing vulnerabilities based on their … [Read more...] about The Ultimate Guide to Vulnerability Management
Cybersecurity-Risk Management
What is Risk Posture?
Risk posture is an organization’s approach to cybersecurity, encompassing its readiness to manage risks and vulnerabilities effectively. It involves identifying, evaluating, and mitigating threats while balancing acceptable risks with necessary controls. Regular assessments of risk posture allow organizations to align their strategies with their overall objectives, providing … [Read more...] about What is Risk Posture?
The Definitive Guide to SASE Security
SASE (Secure Access Service Edge) is a security framework designed to address the challenges of modern, distributed IT environments. It integrates network and security functions in the cloud, providing secure, efficient, and scalable access for users, applications, and data regardless of location or device. By moving beyond traditional perimeter-based security models, SASE … [Read more...] about The Definitive Guide to SASE Security
Threat Spotlight: Bad bots are evolving to become more ‘human’
While decreasing in overall traffic share, malicious bots have become more sophisticated and harder to detect. Advanced bots now constitute 49% of bot activity and often use complex techniques to bypass traditional security measures. These bots can mimic human interactions, evade detection with slow and deliberate actions, and target e-commerce and login systems for fraud and … [Read more...] about Threat Spotlight: Bad bots are evolving to become more ‘human’
DDN Releases Report on Digital, Cybersecurity, and Systemic Risk Governance for 2025
Boardroom governance is vital in overseeing digital, cybersecurity, and systemic risks to safeguard business value and drive investor returns. Effective oversight requires directors with in-depth expertise in data management, cybersecurity, and IT operations, as research has demonstrated the financial benefits of having at least three digitally savvy directors. Boards with such … [Read more...] about DDN Releases Report on Digital, Cybersecurity, and Systemic Risk Governance for 2025
Personal liability: A new trend in cybersecurity compliance?
Cybersecurity compliance is evolving, with recent EU regulations introducing the potential for personal liability among business leaders. Traditionally, compliance penalties targeted organizations, but under the Network and Information Security Directive (NIS 2) and the Digital Operational Resilience Act (DORA), regulators can hold CIOs, CISOs, and other executives personally … [Read more...] about Personal liability: A new trend in cybersecurity compliance?
5 Places to Use a FMEA in Your Quality Process
Failure Mode and Effects Analysis (FMEA) is a structured methodology widely used in industries like manufacturing, pharmaceuticals, and aerospace to identify potential failure points in products or processes and implement preventive measures. Its seven-step process includes defining potential failures, calculating risk priority numbers (RPN), and implementing controls to … [Read more...] about 5 Places to Use a FMEA in Your Quality Process
SecOps integration: Bridging the divide between ISTM and IT security
SecOps is an approach that aligns IT security and IT operations by embedding security practices within ITSM processes. This integration is essential as cybersecurity risks escalate alongside digital innovations. IT security teams focus on maintaining data confidentiality, integrity, and availability, while ITOps teams prioritize service performance and efficiency. SecOps … [Read more...] about SecOps integration: Bridging the divide between ISTM and IT security
Identity management: What you need to know
Identity management (IDM) is an essential process for managing and protecting user identities and access privileges within an organization. By centralizing identity and access management (IAM), organizations can ensure that only verified users access critical resources. IDM systems handle identity creation, entitlement management, and access control, reducing unauthorized … [Read more...] about Identity management: What you need to know
GAO Cybersecurity Program Audit Guide
In its review of the FDIC’s cloud computing security controls, an independent audit by Sikich CPA LLC, commissioned by the FDIC Office of Inspector General, assessed nine key security control areas. While effective security practices were observed in four areas, five exhibited notable control weaknesses. Key vulnerabilities were associated with identity and access management, … [Read more...] about GAO Cybersecurity Program Audit Guide
A Data Protection Approach for Cloud-Native Applications
In this report, the National Institute of Standards and Technology (NIST) outlines a data protection strategy tailored for cloud-native applications. Recognizing the complexities of multi-cloud and hybrid network architectures, the document presents methods to safeguard data as it travels across various systems. A primary focus is on data in transit, a critical aspect of … [Read more...] about A Data Protection Approach for Cloud-Native Applications
Why Do You Need A Cybersecurity Lawyer?
With cyber threats becoming more advanced, businesses face increasing risks of data breaches and unauthorized access to sensitive information. Hackers now use AI-based tools to infiltrate networks, and high-profile cyberattacks in 2024 have affected major companies like TikTok, Microsoft, and Nissan. As data breaches grow in scale, legal consequences become more severe for … [Read more...] about Why Do You Need A Cybersecurity Lawyer?
Risk Register Templates: Enhancing Your Risk Management Strategy
In an uncertain world, managing risks effectively is critical for any business. Risk register templates provide an organized way to document, assess, and track risks, serving as a vital tool in risk management. A risk register is a centralized repository that logs all potential risks during a project’s lifecycle or within an organization. Businesses can identify, assess, and … [Read more...] about Risk Register Templates: Enhancing Your Risk Management Strategy
How to Recognize and Avoid Phishing Scams
Phishing scams are a widespread tactic where scammers use deceptive emails or text messages to trick people into sharing personal information like passwords or account numbers. These messages often look like they come from well-known companies claiming a problem with your account or offering fraudulent deals. Scammers hope you’ll click on links or open attachments, which can … [Read more...] about How to Recognize and Avoid Phishing Scams
The Dynamic Landscape of Cyber Insurance in 2024: Innovations, Opportunities, and Challenges
The cyber insurance landscape in 2024 is marked by rapid growth as digital threats become more complex and frequent. Businesses of all sizes, particularly small and medium-sized enterprises (SMEs), recognize cyber insurance's importance. However, SMEs remain largely uninsured, presenting a significant market opportunity for insurers to develop tailored products that meet their … [Read more...] about The Dynamic Landscape of Cyber Insurance in 2024: Innovations, Opportunities, and Challenges
The 5 Tests Of Controls To Verify Cybersecurity Measures
Controls tests are a critical part of an audit process, ensuring that internal controls are operational and effective in preventing risks and vulnerabilities. These tests help verify the functionality of controls, safeguarding systems against cyber threats. If controls are ineffective, this may indicate a higher risk of control failure, exposing the organization to … [Read more...] about The 5 Tests Of Controls To Verify Cybersecurity Measures
From Trust to Security: Third-party Risk Management Strategies and Challenges
Managing third-party risk has become a critical concern for enterprises, as the complexity of modern IT environments involves numerous external partners. The 2024 CyberRisk Alliance survey revealed that more than half of respondents experienced a third-party security breach in the past 12 months, underscoring the urgent need for improved risk management strategies. Many … [Read more...] about From Trust to Security: Third-party Risk Management Strategies and Challenges
How cyber insurance shapes risk: Ascension and the limits of lessons learned
In May 2024, Ascension, a nonprofit healthcare system, suffered a ransomware attack that disrupted medical services and forced ambulance diversions across several states. Though attributed to the Black Basta cybercriminal group, the attack also highlighted the significant role that cyber insurance plays in managing such crises. As insurers increasingly dictate incident response … [Read more...] about How cyber insurance shapes risk: Ascension and the limits of lessons learned
6 IT risk assessment frameworks compared
IT risk assessment frameworks are critical tools that enable organizations to systematically evaluate and mitigate risks tied to their technology infrastructure, ensuring cybersecurity and compliance. These frameworks are designed to address specific aspects of IT risk, such as data breaches, outages, and regulatory violations, by providing a structured methodology to identify, … [Read more...] about 6 IT risk assessment frameworks compared
5 Ways to Simplify and Speed Third-Party Risk Management Audits
Third-party risk management (TPRM) in IT security is the process of identifying, assessing, and mitigating potential security threats posed by external vendors or partners who have access to an organization’s data or systems. TPRM aims to protect against vulnerabilities introduced by third-party interactions, such as data breaches or compliance failures, by evaluating each … [Read more...] about 5 Ways to Simplify and Speed Third-Party Risk Management Audits