• Compliance requirements like SOC 2 and ISO 27001 can be time-consuming and disruptive but are often necessary for securing business, meeting regulatory demands, and avoiding legal or financial penalties• The importance of compliance depends heavily on industry, with sectors like finance, healthcare, and operational technology (OT) treating it as mission-critical• Compliance … [Read more...] about Does non-compliance in tech really matter?
Cybersecurity-Regulatory
PCI DSS Future-Dated Controls: 7 Critical Changes that Will Shape Your Security Strategy
• PCI DSS 4.0.1 introduces 51 future-dated security controls that will become mandatory on March 31, 2025, requiring updates to password policies, multi-factor authentication (MFA), and payment page integrity.• Organizations must transition to longer, more secure passwords or adopt password-less authentication, eliminate hard-coded credentials, and implement script and … [Read more...] about PCI DSS Future-Dated Controls: 7 Critical Changes that Will Shape Your Security Strategy
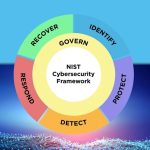
Examples of NIST CSF 2.0 Implementation
The NIST Cybersecurity Framework (CSF) 2.0 provides a comprehensive roadmap for translating cybersecurity principles into real-world practices across diverse sectors. These examples span core governance elements—like aligning cybersecurity strategies with an organization’s mission and risk tolerance—and extend into detailed areas such as asset management, identity and access … [Read more...] about Examples of NIST CSF 2.0 Implementation
Regulating AI: Expert Insights on Compliance, Risk, and Security
AI regulations are developing globally as governments strive to ensure artificial intelligence's safe and ethical use across industries. Frameworks such as the OECD AI Principles and the EU AI Act address issues like transparency, accountability, and risk management. However, navigating compliance presents complexities, especially for organizations integrating AI into their … [Read more...] about Regulating AI: Expert Insights on Compliance, Risk, and Security
The Crucial Difference Between IT Security and Compliance
IT security and compliance are essential components of an organization’s risk management strategy. IT security involves proactive measures to protect systems, data, and networks from cyber threats. It encompasses technical solutions like firewalls, intrusion detection systems, and two-factor authentication, as well as fostering a security-conscious culture through employee … [Read more...] about The Crucial Difference Between IT Security and Compliance
Breaking Into the U.S. Market: Cybersecurity Compliance to Fuel International Growth
Expanding into the U.S. market presents significant growth opportunities for Europe-based cloud service providers (CSPs), but achieving success requires aligning with American cybersecurity compliance expectations. Unlike the EU’s GDPR, the U.S. lacks a comprehensive national privacy law, making adherence to voluntary frameworks such as SOC 2 and ISO 27001 essential for … [Read more...] about Breaking Into the U.S. Market: Cybersecurity Compliance to Fuel International Growth
The backbone of security: How NIST 800-88 and 800-53 compliance safeguards data centers
Data centers are at the forefront of the ever-evolving data storage landscape and require stringent measures to safeguard sensitive information. NIST guidelines, particularly 800-53 and 800-88, provide comprehensive frameworks that protect data throughout its lifecycle. NIST 800-53 focuses on security and privacy controls for IT systems, offering guidance on access control, … [Read more...] about The backbone of security: How NIST 800-88 and 800-53 compliance safeguards data centers
Overview of U.S. Cyber Trust Mark program to address cybersecurity risks in consumer IoT products
The Federal Communications Commission (FCC) is launching the U.S. Cyber Trust Mark program to address cybersecurity risks in consumer IoT products. Devices like smart locks, security cameras, and baby monitors meeting stringent cybersecurity requirements will display the U.S. Cyber Trust Mark, signaling consumers that these products adhere to high standards. This initiative is … [Read more...] about Overview of U.S. Cyber Trust Mark program to address cybersecurity risks in consumer IoT products
110 Compliance Statistics to Know for 2025
The compliance industry is transforming rapidly, driven by heightened cybersecurity threats and regulatory demands. Professionals report a shift from compliance as a mere checkbox exercise to a more strategic function that enhances decision-making and risk management. Over 80% of leaders view compliance as a vital advisory function, with data protection frameworks and vendor … [Read more...] about 110 Compliance Statistics to Know for 2025
Navigating the jungle of cybersecurity regulations
The global cybersecurity regulatory landscape is complicated by multiple, often overlapping, layers of regulations, standards, and industry-specific requirements. National and international rules, such as the GDPR, NIS2, and DORA in the EU, are mandatory, and they form the legal backbone for data protection. These regulations establish high-level principles, demanding companies … [Read more...] about Navigating the jungle of cybersecurity regulations
IoT Cybersecurity: The Broadening Regulatory Landscape
As the digital ecosystem grows, securing IoT networks has become essential to prevent cyberattacks and protect user data, with standards like ISO 27001 and SOC 2 providing foundational frameworks. ISO 27001 focuses on information security management by encouraging organizations to assess and mitigate risks systematically. Meanwhile, SOC 2 is geared toward service providers, … [Read more...] about IoT Cybersecurity: The Broadening Regulatory Landscape
Chevron Pattern Disrupted: The Impact on Cybersecurity Regulations
On June 28, 2024, the Supreme Court’s decision in Loper Bright Enterprises v. Raimondo overturned the long-standing Chevron doctrine, which allowed courts to defer to federal agencies’ interpretations of ambiguous laws. This shift grants courts the primary responsibility for interpreting unclear statutory language, ending a precedent that afforded agencies broad discretion in … [Read more...] about Chevron Pattern Disrupted: The Impact on Cybersecurity Regulations
Implementation Examples for the NIST Cybersecurity Framework 2.0
NIST CSF 2.0 offers actionable implementation examples that help organizations align their cybersecurity risk management decisions with their mission, stakeholder expectations, and legal obligations. For instance, sharing the organization’s mission through statements and strategies can help identify risks that may impede its objectives (GV.OC-01). Internal and external … [Read more...] about Implementation Examples for the NIST Cybersecurity Framework 2.0
Complying with PCI DSS requirements by 2025
If your organization takes online or in person credit card, debit card or related payments, know that Version 4.0.1 of the Payment Card Industry Data Security Standard (PCI DSS), effective April 2024, brings important updates to address modern security challenges in the digital landscape. The updated standard includes 64 requirements, 13 of which are already mandatory, and the … [Read more...] about Complying with PCI DSS requirements by 2025
Just Published: PCI DSS v4.0.1
The PCI Security Standards Council (PCI SSC) has released PCI DSS v4.0.1 as a limited update to the original PCI DSS v4.0, published in March 2022. This revision addresses formatting, typographical errors, and clarifications based on feedback from stakeholders. Importantly, no new or deleted requirements were introduced, making this update a refinement of the previous version … [Read more...] about Just Published: PCI DSS v4.0.1
Defense Department Publishes Proposed Rule requiring contractors working with the federal government to implement cybersecurity requirements
The Defense Department has proposed a new rule requiring contractors working with the federal government to implement the Cybersecurity Maturity Model Certification (CMMC) 2.0 framework. This rule protects unclassified information within the Department of Defense (DoD) supply chain. Contractors must demonstrate compliance with specific cybersecurity levels before being awarded … [Read more...] about Defense Department Publishes Proposed Rule requiring contractors working with the federal government to implement cybersecurity requirements
The Optimal Cyber Risk Management Tools to Streamline DORA Compliance
The Digital Operational Resilience Act (DORA) is designed to protect the EU financial sector from operational disruptions caused by cyber risks. Compliance is required by January 2025, so financial institutions and related third-party vendors must adopt robust ICT risk management, incident reporting, resilience testing, and third-party oversight practices. These regulations add … [Read more...] about The Optimal Cyber Risk Management Tools to Streamline DORA Compliance
Choosing the Right Cybersecurity Frameworks: What Experts Have to Say
Selecting the right cybersecurity framework is crucial for protecting sensitive data and ensuring compliance with industry regulations. Frameworks such as the Center for Internet Security (CIS) Controls, MITRE ATT&CK, and the NIST Cybersecurity Framework offer organizations well-established methodologies for building robust security programs. While these frameworks aren’t … [Read more...] about Choosing the Right Cybersecurity Frameworks: What Experts Have to Say
Align security and compliance to your business goals
In today’s complex business environment, achieving synergy between compliance, security, and business goals is crucial for organizational success. Compliance frameworks provide the regulatory guardrails that ensure operations run within legal boundaries while robust security measures protect assets, intellectual property, and customer data. Simultaneously, aligning these … [Read more...] about Align security and compliance to your business goals
Ultimate List of Cybersecurity Regulations by Industry
Cybersecurity has become a critical concern as industries increasingly rely on digital infrastructure. Governments worldwide have introduced cybersecurity regulations tailored to specific sectors to safeguard sensitive information and prevent cyberattacks. Organizations must understand these regulations to maintain secure digital ecosystems through effective risk management and … [Read more...] about Ultimate List of Cybersecurity Regulations by Industry