As cyberattacks grow more sophisticated and enterprise IT becomes more complex, organizations are finding that traditional, piecemeal security strategies no longer suffice. According to a joint global study conducted by IBM and Palo Alto Networks, the average enterprise juggles 83 different security tools from 29 vendors, creating a fragmented environment where integration gaps … [Read more...] about How Unified Cybersecurity Platforms Add Business Value
Cybersecurity-Continuous Improvement
Achieving Cross-Sector Cybersecurity Performance Goals
In response to growing cyber threats across the U.S. critical infrastructure landscape, the Cybersecurity and Infrastructure Security Agency (CISA) introduced the Cross-Sector Cybersecurity Performance Goals (CPGs). These goals are a practical, risk-based subset of both IT and operational technology (OT) cybersecurity practices developed in collaboration with industry and … [Read more...] about Achieving Cross-Sector Cybersecurity Performance Goals
Cleaning Up the Data Disaster: How Businesses Can Battle Dirty Data
Dirty data costs businesses billions annually, creating inefficiencies and eroding customer trust. Inaccurate data leads to wasted resources, with sales and marketing departments spending up to 32% of their time resolving data issues rather than driving growth. Beyond the financial toll, dirty data harms customer experiences, with 93% of consumers reporting irrelevant … [Read more...] about Cleaning Up the Data Disaster: How Businesses Can Battle Dirty Data
Hyperproof Releases 2024 IT Risk and Compliance Benchmark Report
Hyperproof's 2024 Benchmark Report highlights AI’s dual role in cybersecurity, showing how AI can both enable sophisticated cyberattacks and improve security defenses. While 39% of respondents are concerned about AI risks, 61% see AI as a valuable tool for enhancing cybersecurity measures like control recommendations and documentation reviews. The report emphasizes the … [Read more...] about Hyperproof Releases 2024 IT Risk and Compliance Benchmark Report
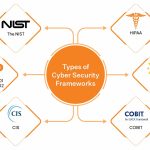
What Experts Have to Say About Choosing the Right Cybersecurity Frameworks
Cybersecurity frameworks such as CIS Controls, MITRE ATT&CK, and NIST CSF provide organizations with structured methodologies to protect sensitive data and offer guidance on security processes. While these frameworks aren't mandatory, like PCI DSS or HIPAA, they help harden systems and strengthen security protocols. The choice of framework depends heavily on an … [Read more...] about What Experts Have to Say About Choosing the Right Cybersecurity Frameworks
Measure Success: Key Cybersecurity Resilience Metrics
Cyber resilience ensures business continuity and profitability by preparing organizations to recover and rebound from inevitable cyberattacks. While cybersecurity focuses on defending against attacks, cyber resilience emphasizes recovery and continuity. Given the sophistication of modern cyber threats, including those enhanced by malicious AI, organizations must strengthen … [Read more...] about Measure Success: Key Cybersecurity Resilience Metrics
Answers to the Most Popular Predictive Prioritization Questions in IT Security
Predictive prioritization is a method of re-prioritizing vulnerabilities based on the likelihood they will be exploited in an attack. This process results in a Vulnerability Priority Rating (VPR), which ranges from zero to ten, indicating a vulnerability's severity and remediation priority. Unlike the Common Vulnerability Scoring System (CVSS), which focuses on potential impact … [Read more...] about Answers to the Most Popular Predictive Prioritization Questions in IT Security
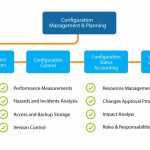
Mastering Configuration Management Across the Modern Enterprise
Security Configuration Management (SCM) is an essential cybersecurity practice for ensuring systems are configured correctly to meet security and compliance standards. SCM helps reduce cyber risks by securing configurations, which involves detecting and remediating misconfigurations across both on-premises and cloud environments. Effective SCM minimizes an organization's attack … [Read more...] about Mastering Configuration Management Across the Modern Enterprise
An Analysis of the Market for Endpoint Security
Radicati's "Endpoint Security Market Quadrant 2024" report analyzes the current landscape of the endpoint security market, categorizing vendors into four distinct segments: Top Players, Trail Blazers, Specialists, and Mature Players. The report comprehensively evaluates each vendor based on their functionality and strategic vision. It aims to help readers understand the … [Read more...] about An Analysis of the Market for Endpoint Security
Migrate Off That Old SIEM Already!
In cybersecurity, the reliance on traditional Security Information and Event Management (SIEM) systems within Security Operations Centers (SOC) remains prevalent even as we navigate through 2024. These systems, pivotal for collecting and analyzing security data, are instrumental in swiftly identifying and responding to threats. However, using outdated SIEM technologies poses … [Read more...] about Migrate Off That Old SIEM Already!
A Guide to Effective Cloud Privileged Access Management
The landscape of cloud security has evolved significantly, transitioning from skepticism among enterprises to becoming a widely accepted and secure platform for organizations of various sizes. However, securing the cloud environment is more complex than it might seem; it requires a nuanced approach to manage privileged access effectively. The article emphasizes the complexity … [Read more...] about A Guide to Effective Cloud Privileged Access Management
IoT Security Labeling Improving, But More Collaboration Needed
In the article "IoT Security Labeling Improving, But More Collaboration Needed," Steve Hanna writes about the recent advancement in consumer IoT device security through the U.S. Cyber Trust Mark program. Based on the criteria defined in NIST IR 8425, this program offers an objective way for consumers to identify products with a verified baseline level of security. Hanna argues … [Read more...] about IoT Security Labeling Improving, But More Collaboration Needed