Hitachi's 2024 Information Security Report exemplifies how a global organization can develop and execute a cohesive cybersecurity strategy. While not marketing specific products or services, the report aims to inspire confidence in the Hitachi Group's ability to protect its information systems, products, and supply chain. Though it references fiscal year 2023 initiatives, the … [Read more...] about Hitachi Group Releases Information Security Report 2024 on How to Create IT Security System for Organizations
NIS2 vs ISO 27001: What’s the Difference?
NIS2 and ISO 27001 are distinct cybersecurity frameworks catering to different organizational needs. NIS2 targets critical infrastructure sectors like energy, healthcare, and banking, ensuring they remain resilient against cyber incidents to protect societal and economic stability. In contrast, ISO 27001 provides a globally recognized framework for implementing an Information … [Read more...] about NIS2 vs ISO 27001: What’s the Difference?
Cybersecurity Frameworks Explained
Cybersecurity frameworks like CIS Critical Security Controls (CIS CSC) and NIST Cybersecurity Framework (NIST CSF) help organizations navigate the complexities of IT security. These frameworks emerged around 2013 to address the growing need for structured cybersecurity practices. They guide identifying adequate controls and safeguarding computing infrastructure, data, and user … [Read more...] about Cybersecurity Frameworks Explained
How to Measure and Benchmark Cybersecurity Events
Cybersecurity excellence is achieved through leadership commitment, ongoing training, proactive risk management, effective incident response, and continuous improvement. These elements integrate cybersecurity into an organization’s broader strategy, ensuring resilience against an ever-changing threat landscape. Key performance indicators (KPIs) are pivotal in quantifying … [Read more...] about How to Measure and Benchmark Cybersecurity Events
Distributing Ownership of an Organization’s Cybersecurity Risks
Cybersecurity has evolved beyond being a technological risk to encompass organization-wide responsibility, driven by escalating threats and stringent regulations like the EU’s NIS 2 and SEC disclosure rules. Managing cybersecurity requires coordinated efforts across all levels of an organization, ensuring asset owners follow best practices and address identified risks within a … [Read more...] about Distributing Ownership of an Organization’s Cybersecurity Risks
What Companies Can Do To Protect Against Cyberattacks … and the Litigation That Often Follows
Cybersecurity threats are expanding due to factors like digitization, cloud computing, and AI, prompting boards of directors to prioritize cybersecurity oversight. Recent SEC regulations mandate public companies to disclose their board’s role in managing cybersecurity risks, including identifying responsible committees. This shift and legal pressures exemplified by recent … [Read more...] about What Companies Can Do To Protect Against Cyberattacks … and the Litigation That Often Follows
Developing an ISO 27001 Information Security Policy
Developing an ISO 27001 Information Security Policy is critical for organizations seeking to establish and maintain an effective ISMS. The policy is a high-level document outlining an organization's commitment to information security and provides a framework for protecting its data and assets. According to Clause 5.2 of ISO 27001:2022, top management must establish an … [Read more...] about Developing an ISO 27001 Information Security Policy
Understanding ISO 27001 Key Performance Indicators (KPIs) and Their Benefits
ISO 27001 certification provides organizations with a framework for establishing, implementing, and continually improving their Information Security Management System (ISMS). ISO 27001 Key Performance Indicators (KPIs) are crucial to measuring the effectiveness of an ISMS. These metrics provide insights into whether security objectives are being met and whether the system … [Read more...] about Understanding ISO 27001 Key Performance Indicators (KPIs) and Their Benefits
What is Cyber Supply Chain Risk Management?
Cyber Supply Chain Risk Management (C-SCRM) identifies, assesses, and mitigates cybersecurity risks within an organization’s supply chain. By encompassing risks from procurement tools, third-party vendors, and developers, C-SCRM extends beyond traditional third-party risk management. Its lifecycle involves vendor vetting, assessing security postures during acquisition, … [Read more...] about What is Cyber Supply Chain Risk Management?
A Guide to Developing a Business or Retail Supply Chain Cybersecurity Risk Management Plan
Retail supply chains rely heavily on third-party suppliers, creating potential cybersecurity vulnerabilities that malicious actors can exploit. Risks are categorized into supplier, supply, and service risks, each requiring tailored strategies to mitigate threats. High-risk suppliers, such as those handling critical software or sensitive data, necessitate rigorous evaluation and … [Read more...] about A Guide to Developing a Business or Retail Supply Chain Cybersecurity Risk Management Plan
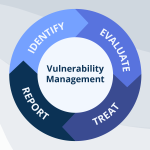
The Ultimate Guide to Vulnerability Management
Vulnerability management (VM) is a proactive approach to identifying, evaluating, and mitigating security vulnerabilities within an organization's systems. By continuously scanning and monitoring environments, VM helps minimize attack surfaces and protect critical assets. A risk-based approach, RBVM, enhances traditional methods by prioritizing vulnerabilities based on their … [Read more...] about The Ultimate Guide to Vulnerability Management
What is Risk Posture?
Risk posture is an organization’s approach to cybersecurity, encompassing its readiness to manage risks and vulnerabilities effectively. It involves identifying, evaluating, and mitigating threats while balancing acceptable risks with necessary controls. Regular assessments of risk posture allow organizations to align their strategies with their overall objectives, providing … [Read more...] about What is Risk Posture?
Why AI Falls Short in Regulatory Consulting
AI's rapid advancements have transformed industries through automation and data analysis, yet its application in regulatory consulting reveals significant shortcomings. Regulatory frameworks are complex, jurisdiction-specific, and often require nuanced interpretation that AI struggles to provide. While AI excels at basic data parsing and identifying patterns, it cannot grasp … [Read more...] about Why AI Falls Short in Regulatory Consulting
Risk Management Uncovered: Common Sense Approaches and Practical Tools (Podcast)
This podcast explores the power of Pareto charts in quality management, emphasizing their effectiveness in identifying the root causes of operational issues. Rooted in the 80/20 principle, Pareto charts illustrate how a small percentage of causes can account for most problems, making them indispensable for process improvement. Their simplicity and clarity make them ideal for … [Read more...] about Risk Management Uncovered: Common Sense Approaches and Practical Tools (Podcast)
Pareto Chart: How to Use It to Identify Root Causes
Pareto charts are a practical tool for analyzing root causes in business processes, based on the 80/20 principle, which states that 80% of problems often arise from 20% of causes. This makes them particularly effective for prioritizing issues and focusing on the most impactful solutions. Their simplicity and flexibility make them a go-to tool for Lean Six Sigma practices and … [Read more...] about Pareto Chart: How to Use It to Identify Root Causes
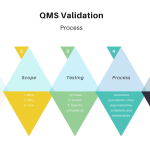
Critical Aspects of Quality Management Systems: Focusing on the Validation Process
In regulated industries such as pharmaceuticals, medical devices, and food manufacturing, validation of Quality Management Systems (QMS) ensures compliance with standards like FDA 21 CFR Part 11, ISO 13485, and EU MDR. (These tools, while not required in less regulated industries, are valuable for maintaining product/service integrity and can be used as models there.) … [Read more...] about Critical Aspects of Quality Management Systems: Focusing on the Validation Process
15 Top Quality KPIs in Manufacturing
Tracking and optimizing Key Performance Indicators (KPIs) is vital for manufacturing success, ensuring quality and efficiency. Metrics such as First Pass Yield (FPY) gauge production efficiency by measuring the percentage of products completed correctly on the first attempt. Defects Per Unit (DPU) and Scrap Rate monitor product defects and material waste, helping identify … [Read more...] about 15 Top Quality KPIs in Manufacturing
Data Speaks for Itself: Data Validation – Data Accuracy Imposter or Assistant?
Data validation and accuracy are often conflated in data quality management but serve different purposes. Validation identifies incorrect values through rule-based tests, while accuracy requires comparing data to authoritative sources. Validation alone cannot guarantee accuracy, as it may overlook errors in seemingly valid records. Achieving true accuracy demands … [Read more...] about Data Speaks for Itself: Data Validation – Data Accuracy Imposter or Assistant?
Checklist of Mandatory Documentation Required by ISO 9001:2015
ISO 9001:2015 streamlines documentation requirements compared to earlier versions, mandating fewer procedures but emphasizing the importance of key records to support QMS operations. Mandatory documents include the scope of the QMS, quality policy, and objectives, while required records range from design outputs to nonconformity logs. These ensure compliance and aid in … [Read more...] about Checklist of Mandatory Documentation Required by ISO 9001:2015
Mastering Leadership in Quality Management: ISO 9001 Clause 5
ISO 9001 Clause 5 serves as a cornerstone for quality management, highlighting the importance of leadership in driving the success of a QMS. Leaders are tasked with actively participating in developing and maintaining the QMS, establishing clear quality policies and objectives, and ensuring sufficient resources are allocated to meet these goals. By aligning the QMS with the … [Read more...] about Mastering Leadership in Quality Management: ISO 9001 Clause 5