Conducting an IT risk assessment is essential for organizations facing increasing cyber threats, with cyberattacks occurring every 40 seconds and ransomware attacks rising rapidly. An IT risk assessment identifies vulnerabilities within an organization’s information systems, networks, and data, helping leaders understand potential financial and operational impacts. Such … [Read more...] about How to Perform a Successful IT Risk Assessment
Regulating AI: Expert Insights on Compliance, Risk, and Security
AI regulations are developing globally as governments strive to ensure artificial intelligence's safe and ethical use across industries. Frameworks such as the OECD AI Principles and the EU AI Act address issues like transparency, accountability, and risk management. However, navigating compliance presents complexities, especially for organizations integrating AI into their … [Read more...] about Regulating AI: Expert Insights on Compliance, Risk, and Security
10 Best Vulnerability Assessment and Penetration Testing (VAPT) Tools in 2025
Vulnerability Assessment and Penetration Testing (VAPT) tools are essential for organizations aiming to strengthen their cybersecurity defenses. Vulnerability assessments identify potential weaknesses in systems, while penetration testing simulates attacks to determine if these vulnerabilities are exploitable. Together, they provide a comprehensive security evaluation that … [Read more...] about 10 Best Vulnerability Assessment and Penetration Testing (VAPT) Tools in 2025
SOC 2 vs ISO 27001: What’s the Difference and Which Standard Do You Need?
SOC 2 and ISO 27001 are the most recognized frameworks for information security compliance. SOC 2, developed by the AICPA, focuses on protecting customer data through five Trust Services Criteria: Security, Availability, Confidentiality, Privacy, and Processing Integrity. It is particularly popular among US-based companies, offering flexibility in selecting applicable criteria. … [Read more...] about SOC 2 vs ISO 27001: What’s the Difference and Which Standard Do You Need?
Integrating Cybersecurity Frameworks into IT Security: A Comprehensive Analysis
Organizations face increasingly sophisticated cyber threats ranging from malware and ransomware to insider threats and state-sponsored attacks. As digital environments evolve with cloud computing and interconnected systems, cybersecurity frameworks provide structured approaches to risk management, compliance, and threat mitigation. The NIST Cybersecurity Framework emphasizes … [Read more...] about Integrating Cybersecurity Frameworks into IT Security: A Comprehensive Analysis
OWASP Releases Updated 2025 Top 10 Risks for LLMs
The OWASP Foundation has released the 2025 edition of its Top 10 Risks for LLM Applications and Generative AI, addressing the changing threat landscape as organizations increasingly adopt generative AI technologies. This refreshed list provides updated insights into vulnerabilities across development, deployment, and management phases, helping developers and security … [Read more...] about OWASP Releases Updated 2025 Top 10 Risks for LLMs
Artificial Intelligence and Cybersecurity: Balancing Risks and Rewards
AI technologies offer significant business benefits but introduce unique cybersecurity challenges that organizations must address to innovate safely. A risk-based approach is essential, involving diverse stakeholders across legal, technology, HR, compliance, and business units. Creating an inventory of AI applications helps organizations track usage, mitigate risks of "shadow … [Read more...] about Artificial Intelligence and Cybersecurity: Balancing Risks and Rewards
The Crucial Difference Between IT Security and Compliance
IT security and compliance are essential components of an organization’s risk management strategy. IT security involves proactive measures to protect systems, data, and networks from cyber threats. It encompasses technical solutions like firewalls, intrusion detection systems, and two-factor authentication, as well as fostering a security-conscious culture through employee … [Read more...] about The Crucial Difference Between IT Security and Compliance
The Benefits of CISM Certification and How to Pass the CISM Exam
The Certified Information Security Manager (CISM) certification, offered by ISACA, validates an information security professional’s ability to design, manage, and assess an organization’s information security program. CISM focuses on four key domains: Information Security Governance, Information Risk Management, Information Security Program Development and Management, and … [Read more...] about The Benefits of CISM Certification and How to Pass the CISM Exam
Design and Implementation of an Open-Source Security Operations Center for Effective Cyber Threat Detection and Response
This study addresses the growing need for effective cybersecurity solutions by designing an open-source Security Operations Center (SOC) tailored for small and medium-sized enterprises. Recognizing the increasing frequency and sophistication of cyberattacks—ranging from ransomware to SQL injections—the proposed architecture integrates multiple components to ensure comprehensive … [Read more...] about Design and Implementation of an Open-Source Security Operations Center for Effective Cyber Threat Detection and Response
AI Security: Risks, Frameworks, and Best Practices
AI security encompasses a range of measures designed to protect AI systems from unauthorized access, manipulation, and malicious attacks. These safeguards ensure the integrity, privacy, and proper functioning of AI applications, which are increasingly integral to modern operations. The risks extend beyond technical vulnerabilities to ethical concerns, such as bias and … [Read more...] about AI Security: Risks, Frameworks, and Best Practices
How to create a third-party risk management policy
Developing an effective third-party risk management policy is essential for organizations seeking to mitigate risks from suppliers, vendors, and external partners. These risks include data breaches, operational failures, regulatory violations, and reputational harm. Leveraging NIST’s Cybersecurity Framework (CSF) offers a flexible and globally recognized approach to structuring … [Read more...] about How to create a third-party risk management policy
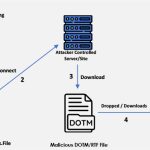
The Mechanics of Remote Template Injection Attack
Remote Template Injection is a sophisticated cyberattack method that exploits Microsoft Word’s ability to load templates from remote servers. Attackers embed a malicious template link in a Word document, enabling the execution of harmful macros without directly embedding them in the file. This allows the decoy document to bypass traditional security measures, including email … [Read more...] about The Mechanics of Remote Template Injection Attack
CMMC 2.0: Your Comprehensive Guide to Certification and Compliance
CMMC 2.0 ensures that any organization working with the Department of Defense (DoD) and handling Federal Contract Information (FCI) or Controlled Unclassified Information (CUI) meets stringent cybersecurity requirements. The updated framework, based on NIST 800-171 standards, reduces complexity by consolidating five certification levels into three. This revision benefits small … [Read more...] about CMMC 2.0: Your Comprehensive Guide to Certification and Compliance
ISO 9001:2025 Revision – What you need to know
The upcoming ISO 9001:2026 revision is a crucial update for quality management professionals, aiming to reflect significant changes in business, technology, and global challenges since the last major update in 2015. The revision process is currently in progress, with Working Group 29 reviewing feedback on the first Committee Draft (CD) and preparing for the Draft International … [Read more...] about ISO 9001:2025 Revision – What you need to know
14 Examples of Quality Metrics in Manufacturing for Product Quality Assurance
Measuring quality metrics in manufacturing is essential for identifying inefficiencies and improving product standards. These metrics are divided into process metrics (evaluating production efficiency), product metrics (assessing defect rates and customer satisfaction), maintenance metrics (ensuring equipment reliability), and supplier quality metrics (monitoring material … [Read more...] about 14 Examples of Quality Metrics in Manufacturing for Product Quality Assurance
AI in (Quality) Procurement
Artificial intelligence is transforming procurement by automating processes, analyzing large datasets, and generating actionable insights. Narrow AI, the primary form used in procurement, enables spend classification, vendor risk assessment, quality control, contract analysis, and supplier discovery. Machine learning refines data categorization, while natural language … [Read more...] about AI in (Quality) Procurement
The ISO 9001:2015 Quality Management System Standard: Companies’ Drivers, Benefits and Barriers to Its Implementation
A survey of 493 ISO 9001-certified Italian companies reveals that the standard is widely recognized, especially in northern Italy, where economic development is highest. The study finds that most businesses have been certified for over seven years, indicating a long-standing quality culture. Companies transitioning from ISO 9001:2008 to the 2015 version acknowledge its emphasis … [Read more...] about The ISO 9001:2015 Quality Management System Standard: Companies’ Drivers, Benefits and Barriers to Its Implementation
Revolutionizing procurement: Leveraging data and AI for strategic advantage
Procurement is undergoing a significant transformation, with data and AI enabling organizations to optimize sourcing strategies, predict market fluctuations, and automate supplier management. AI-driven tools help both quality and procurement teams analyze spend, forecast demand, and assess external risks like price volatility or supply chain disruptions. Digital dashboards and … [Read more...] about Revolutionizing procurement: Leveraging data and AI for strategic advantage
How to Identify Non-Conformance at Work
Non-conformance in the workplace occurs when processes or products fail to meet specified requirements, leading to inefficiencies, safety risks, or regulatory violations. It can be categorized into minor and significant non-conformances, with minor issues typically involving isolated documentation or procedural errors. In contrast, major non-conformances include critical … [Read more...] about How to Identify Non-Conformance at Work