This article from a China-focused contract manufacturing sourcing company describes prototyping as a crucial step in product development. They describe their experience in prototyping as It transforms concepts into tangible models that allow teams to explore design elements, functionality, and user experience. Prototypes are invaluable for identifying design flaws or functional … [Read more...] about Defining Quality Standards: A Guide for Product Development Prototypes
Compliance Management and the Role of Policies and Procedures
Compliance management is essential for many organizations to maintain legal and ethical standards, avoid penalties, and uphold operational integrity. By setting a clear framework through policies and procedures, organizations can effectively guide employees to meet compliance requirements. Compliance management encompasses industry-specific regulations, standards, and … [Read more...] about Compliance Management and the Role of Policies and Procedures
The paradox of data quality
The paradox of data quality lies in balancing accuracy with practicality. While quality data is critical for informed decision-making, striving for perfection is costly and unsustainable. According to Pepar Hugo, Senior Data Engineer at Lumenalta, an excessive focus on flawless data can create “analysis paralysis,” consuming valuable resources that could be better allocated to … [Read more...] about The paradox of data quality
Data Quality Management: Tools, Implementation Strategies, and Best Practices
Data Quality Management (DQM) is crucial in supporting strategic decision-making for marketing teams by ensuring that the data they rely on is accurate, consistent, and up-to-date. Through practices like data cleansing, validation, and integration, DQM helps teams focus on analyzing and applying insights rather than being bogged down by data inaccuracies. This framework … [Read more...] about Data Quality Management: Tools, Implementation Strategies, and Best Practices
Getting the Most Out of an EQMS (Webcast)
The webcast discusses strategies for maximizing QMS functionality, focusing on improving integration, training, and reporting for seamless quality management. One company shared its process of implementing a QMS software system's modules, highlighting key integrations with systems like MES and Active Directory to streamline production, automate access control, and track … [Read more...] about Getting the Most Out of an EQMS (Webcast)
FMEA in the Age of Industry 4.0
In the context of Industry 4.0, Failure Mode and Effects Analysis (FMEA) is adapting to address the increased complexity of manufacturing processes. Traditionally, FMEA assessed potential failure modes by analyzing severity, occurrence, and detection, which produced a Risk Priority Number (RPN) to guide risk mitigation efforts. However, this approach has limitations in modern … [Read more...] about FMEA in the Age of Industry 4.0
Book Review: “Measuring and Managing Information Risk”
Measuring and Managing Information Risk: A FAIR Approach, Second Edition is a detailed resource for understanding and applying the Factor Analysis of Information Risk (FAIR) methodology, a trusted framework for measuring and managing information risk across various organizational contexts. With over a decade of development and practical application, FAIR has become a … [Read more...] about Book Review: “Measuring and Managing Information Risk”
Building a Culture of Cyber Resilience in Manufacturing
The manufacturing sector has become a prime target for cyberattacks due to its swift digital transformation and reliance on interconnected supply chains. As digital technologies like the industrial Internet of Things (IIoT) and artificial intelligence (AI) integrate into operational processes, the risk of ransomware attacks and other cyber threats has grown significantly. These … [Read more...] about Building a Culture of Cyber Resilience in Manufacturing
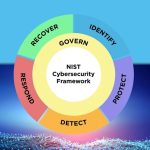
Implementation Examples for the NIST Cybersecurity Framework 2.0
NIST CSF 2.0 offers actionable implementation examples that help organizations align their cybersecurity risk management decisions with their mission, stakeholder expectations, and legal obligations. For instance, sharing the organization’s mission through statements and strategies can help identify risks that may impede its objectives (GV.OC-01). Internal and external … [Read more...] about Implementation Examples for the NIST Cybersecurity Framework 2.0
Should Cybersecurity Leadership Finally be Professionalized?
The role of the Chief Information Security Officer (CISO) has evolved significantly, as they now face external cyber threats and internal challenges, such as inadequate resources, increasing regulations, and personal liability for security failures. This has sparked renewed interest in the idea of professionalizing the field of cybersecurity leadership. Advocates argue that a … [Read more...] about Should Cybersecurity Leadership Finally be Professionalized?
The Perilous Role of the CISO: Navigating Modern Minefields
The role of the Chief Information Security Officer (CISO) has become increasingly difficult as they contend with a constantly shifting threat landscape, regulatory complexities, and heightened legal liabilities. Originally tasked with protecting networks and systems, CISOs now face broader challenges, including managing compliance with evolving regulations and dealing with … [Read more...] about The Perilous Role of the CISO: Navigating Modern Minefields
12 Best Practices for a Corporate Firewall Review
A corporate firewall review is a critical process for assessing and enhancing your organization’s network security by evaluating firewall rules and configurations and their alignment with business needs and risk tolerance. Modern businesses often utilize multiple firewalls from different vendors, complicating maintaining a consistent security posture. Regular reviews help … [Read more...] about 12 Best Practices for a Corporate Firewall Review
What is Access Control? Types, Importance & Best Practices
Access control is a security mechanism that limits access to an organization’s resources, ensuring that only authorized individuals can view or use sensitive data. It plays a critical role in safeguarding information and complying with GDPR, HIPAA, and PCI DSS regulations. By restricting access to data and systems, businesses can protect themselves from data breaches and other … [Read more...] about What is Access Control? Types, Importance & Best Practices
Cyber Risk Management in the C‑Suite
Ivanti’s report explores how cybersecurity leaders adapt to an increasingly sophisticated threat landscape and how CISOs can align cybersecurity strategies with broader business goals. The survey of over 3,000 IT and security professionals revealed a critical issue: executive overconfidence in the organization's ability to manage cyber risks. Sixty percent of executives outside … [Read more...] about Cyber Risk Management in the C‑Suite
CISO Report: Emerging trends, threats and strategies for today’s security leaders
Splunk’s CISO Report outlines the evolving role of Chief Information Security Officers (CISOs) and their challenges in today’s complex cybersecurity landscape. As cyberattack threats grow, CISOs are increasingly positioned as strategic leaders within their organizations. Nearly half of all CISOs now report directly to their CEO, a significant shift in their role, highlighting … [Read more...] about CISO Report: Emerging trends, threats and strategies for today’s security leaders
Why Do You Need A Cybersecurity Lawyer?
With cyber threats becoming more advanced, businesses face increasing risks of data breaches and unauthorized access to sensitive information. Hackers now use AI-based tools to infiltrate networks, and high-profile cyberattacks in 2024 have affected major companies like TikTok, Microsoft, and Nissan. As data breaches grow in scale, legal consequences become more severe for … [Read more...] about Why Do You Need A Cybersecurity Lawyer?
Risk Register Templates: Enhancing Your Risk Management Strategy
In an uncertain world, managing risks effectively is critical for any business. Risk register templates provide an organized way to document, assess, and track risks, serving as a vital tool in risk management. A risk register is a centralized repository that logs all potential risks during a project’s lifecycle or within an organization. Businesses can identify, assess, and … [Read more...] about Risk Register Templates: Enhancing Your Risk Management Strategy
How to Recognize and Avoid Phishing Scams
Phishing scams are a widespread tactic where scammers use deceptive emails or text messages to trick people into sharing personal information like passwords or account numbers. These messages often look like they come from well-known companies claiming a problem with your account or offering fraudulent deals. Scammers hope you’ll click on links or open attachments, which can … [Read more...] about How to Recognize and Avoid Phishing Scams
Complying with PCI DSS requirements by 2025
If your organization takes online or in person credit card, debit card or related payments, know that Version 4.0.1 of the Payment Card Industry Data Security Standard (PCI DSS), effective April 2024, brings important updates to address modern security challenges in the digital landscape. The updated standard includes 64 requirements, 13 of which are already mandatory, and the … [Read more...] about Complying with PCI DSS requirements by 2025
Just Published: PCI DSS v4.0.1
The PCI Security Standards Council (PCI SSC) has released PCI DSS v4.0.1 as a limited update to the original PCI DSS v4.0, published in March 2022. This revision addresses formatting, typographical errors, and clarifications based on feedback from stakeholders. Importantly, no new or deleted requirements were introduced, making this update a refinement of the previous version … [Read more...] about Just Published: PCI DSS v4.0.1