Boeing has faced significant scrutiny over its manufacturing practices, which have recently been linked to several quality and reliability issues, including the high-profile 737 Max series air crashes and a near-disaster involving an Alaska Airlines Max 9. Key factors contributing to these incidents include accepting substandard parts from suppliers, deferred problem-solving to … [Read more...] about What are Boeing’s Bad Manufacturing Habits Leading to Quality and Reliability Risks?
Root Cause Analysis 101
This 36-page primer on Root cause analysis (RCA) from audit software supplier EASE covers this essential method in quality management. RCA is used to diagnose the fundamental reason for faults or problems. Five common RCA methods are Pareto Charts, The 5 Whys, Fishbone Diagrams, Scatter Plots, and Failure Mode and Effects Analysis (FMEA). This structured approach helps identify … [Read more...] about Root Cause Analysis 101
Force Measurement and AI: Predicting Product Failure
Ensuring that products meet rigorous standards for quality and reliability is paramount, making force measurement a critical aspect of manufacturing. This testing method allows quality control professionals to verify that products are robust and comply with specified standards before they reach the market. Integrating Artificial Intelligence (AI) into this process has … [Read more...] about Force Measurement and AI: Predicting Product Failure
What is a Fishbone Diagram?
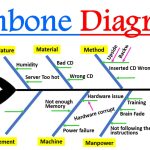
Fishbone diagrams, also known as Ishikawa diagrams or cause-and-effect diagrams, are visual tools used to systematically identify potential factors causing an overall effect, particularly in troubleshooting and quality improvement sessions. The diagram looks like the skeleton of a fish, where the problem or effect is the fish's head, and the bones branching off the spine … [Read more...] about What is a Fishbone Diagram?
What is COPQ (Cost of Poor Quality)?
The Cost of Poor Quality (COPQ) encapsulates the financial costs of failing to meet production and service delivery standards. These costs are broadly categorized into four types: prevention costs, appraisal costs, internal failure costs, and external failure costs. Prevention costs involve expenditures to prevent defects from occurring, such as training and quality planning. … [Read more...] about What is COPQ (Cost of Poor Quality)?
Critical failure factors for Quality 4.0: an exploratory qualitative study
Adoption of Quality 4.0 (Q4.0) in organizations is challenging. Identifying the critical failure factors (CFFs) can lead to more effective implementation of Q4.0 initiatives. Researchers used a qualitative research methodology involving in-depth interviews with quality managers and executives to help establish the CFFs associated with Q4.0. This approach enriches the existing … [Read more...] about Critical failure factors for Quality 4.0: an exploratory qualitative study
Mutual combination of selected principles and technologies of Industry 4.0 and quality management methods
A detailed exploration of integrating Industry 4.0 technologies and principles with quality management methods, specifically through Failure Mode and Effects Analysis (FMEA), can be presented using a "Smart Factory Line" testbed. This method aims to verify the feasibility of applying FMEA in a complex technical system and to demonstrate the potential of integrating Industry 4.0 … [Read more...] about Mutual combination of selected principles and technologies of Industry 4.0 and quality management methods
AI in operational excellence
Artificial intelligence (AI) is transforming business operations by enhancing efficiency, minimizing waste, and supporting continuous improvement. AI and its subfields like machine learning (ML), deep learning, and automation augment traditional operational excellence strategies such as Lean, Six Sigma, and total quality management (TQM). For instance, AI aids in identifying … [Read more...] about AI in operational excellence
Who’s interpretation of ISO standards matters?
One interpretation of AS/ISO standards revolves around understanding who holds the authority to interpret these standards within organizations and the implications of such interpretations. This recent forum discussion begins by questioning how different interpretations of standards, particularly concerning competency, are handled within organizations and the role of quality … [Read more...] about Who’s interpretation of ISO standards matters?
Book Review: Cybersecurity Architect’s Handbook
In the rapidly evolving world of digital security, the "Cybersecurity Architect's Handbook" emerges as an essential resource for novice and experienced cybersecurity professionals. This comprehensive guide is crafted to assist readers in mastering the intricate aspects of cybersecurity architecture. It offers a step-by-step approach to transitioning from entry-level roles to … [Read more...] about Book Review: Cybersecurity Architect’s Handbook
Cyber Risk Quantification Guide: Measurement & Mitigation
Cybersecurity has become a central concern for organizations worldwide, with a reported 48% increase in cyberattacks in 2023 compared to the previous year. This surge in cybercrime, expected to cost the global market an additional 5.7 trillion U.S. dollars by 2028, underscores the urgent need for effective cybersecurity measures. As cyber threats evolve in sophistication, from … [Read more...] about Cyber Risk Quantification Guide: Measurement & Mitigation
A Complete Guide to OT Security Compliance
The importance of operational technology (OT) security compliance has escalated due to the increasing interconnection between IT and OT systems, making critical infrastructures more vulnerable to cyber threats. This interconnectivity offers substantial benefits but also introduces significant risks, highlighting the necessity for a comprehensive approach to OT security … [Read more...] about A Complete Guide to OT Security Compliance
Risk and Regulation: Preparing for the Era of Cybersecurity Compliance
The upcoming year marks a critical period in cybersecurity as several new regulations to enhance cybersecurity standards across various sectors are set to roll out. These regulations, which include the EU's NIS2 Directive and the Digital Operational Resilience Act (DORA), mandate that companies not only adhere to strict cybersecurity practices but also ensure that their key … [Read more...] about Risk and Regulation: Preparing for the Era of Cybersecurity Compliance
New compensation trends in the cybersecurity sector
The "Cybersecurity Staff Compensation Benchmark Report 2023-2024" from IANS Research and Artico Search provides crucial insights into compensation, diversity, work conditions, and job satisfaction among cybersecurity professionals. The report, compiled from survey responses from over 560 staff across various industries in the U.S. and Canada and interviews from 100 CISOs, … [Read more...] about New compensation trends in the cybersecurity sector
A Security Leader’s Guide to Crosswalk Compliance Frameworks
In the rapidly evolving regulatory environment, it's increasingly crucial for organizations to achieve compliance across multiple frameworks. This involves aligning cybersecurity measures with various regulatory requirements such as SOC2, PCI, and GDPR to create a unified strategy that prevents duplication of efforts and reduces errors. Integrating cybersecurity with … [Read more...] about A Security Leader’s Guide to Crosswalk Compliance Frameworks
Why governance, risk, and compliance must be integrated with cybersecurity
Integrating cybersecurity into governance, risk, and compliance (GRC) frameworks is becoming increasingly essential as organizations face evolving threats and stringent regulatory demands. Factors such as cloud adoption, hybrid workforces, and the widespread use of generative AI drive the need for comprehensive risk management that encompasses cybersecurity. This integration … [Read more...] about Why governance, risk, and compliance must be integrated with cybersecurity
5 Ways CISOs Can Navigate Their New Business Role
Today's Chief Information Security Officers (CISOs) are confronted with many challenges, both from within their organizations and external threats. The role of the CISO has evolved significantly; they are now expected not only to manage and implement new technologies and improve team skills and morale but also to assume a greater leadership role in reducing compliance risks and … [Read more...] about 5 Ways CISOs Can Navigate Their New Business Role
Understanding CyberRisk Quantification: A Buyer’s Guide
The cyber risk landscape is evolving into a complex and dynamic challenge for organizations, which often struggle to allocate sufficient resources to effectively manage cyber risks without neglecting other critical business or operational needs. Effective cyber risk management programs are essential, relying heavily on the capability to precisely measure cyber risks to … [Read more...] about Understanding CyberRisk Quantification: A Buyer’s Guide
Crafting and Communicating Your Cybersecurity Strategy for Board Buy-In
In today's digital era, cybersecurity has emerged as a fundamental component of corporate strategy and risk management, necessitating a strategic approach in its communication, especially to board members. Cybersecurity is no longer just a technical issue but a crucial part of boardroom discussions due to the increasing frequency of cyber threats, which can disrupt business … [Read more...] about Crafting and Communicating Your Cybersecurity Strategy for Board Buy-In
Data Privacy Laws Around the World: A Comprehensive Guide
Data privacy has become a critical issue for organizations globally as they navigate an increasingly digital landscape. As the volume of personal data collected and processed grows, so does the importance of protecting this information. Governments worldwide have responded by enacting data privacy laws to secure individuals' details and maintain public trust. These laws seek to … [Read more...] about Data Privacy Laws Around the World: A Comprehensive Guide